Security Policies
Contents
Security Policies
In computer network security area, security policies are one of the important topics to research on. In this article, I will explain to you what security policies are, the nature of the policies and the mechanisms. These topics will be covered along with necessarily detailed examples too. Keep reading to know more.
What are security policies?
Security policies are the definition which partitions the system. These partitions are divided into two categories. Authorized or secure state, the area which the system can safely enter. And the unauthorized area or the non-secure area defines the states which the system cannot enter. And it is the developer’s job to assure to build a system which only enters authorized states and never enters to any unauthorized states.
Confidentiality
Confidentiality is one of the pillars of security policies. And it explains keeping the data and other resources hidden from the public and only visible to the authorized. If I explain to you about confidentiality using mathematics, is X is a set of entities and L is a set of information. L should have the confidentiality with respect to X If no entity which includes in the set X can obtain any piece of information from the set L. Moreover, this L can be disclosed to others too.
So, if the X is students and if L is the exam answers, L is confidential with respect to X if the students cannot get the answers for the exam. But there is another point. These exam results are visible or can be obtained after the exam. So the key point is, this confidentiality has a time frame which is valid. The time frame can be from a short time to an infinity time too.
Integrity
Now, let us move to the integrity factor. This is also a pillar of security. There are three types of integrities. Data integrity explains the data or the information cannot be modified without authorization. The data integrity is a measurement of the trust of data of conveyance and protection. Origin integrity is about having an authentication for the data. Which meant that information should have an originated resource or an identity. And the assurance integrity means the relevant information or the resource should function the way it is supposed to be. Or else it is also an integrity violation.
Availability
Mainly availability assures the data to be available for the authorized at any given time. The availability divides into two. One is traditional which explains whether the data is available for the entity or not. It is very straightforward. A student cannot have access to their marks. And they are only allowed to access their grades. This is an example of traditional availability.
There is another type of availability. Which is the quality of service. This defines the promised level of access. In this availability, the entity is promised a certain amount or a bandwidth of data. They may not have access to all. But they are allowed to access a part of it.
What are the policy models?
Policy model is an abstract description. This information has very broad coverage and does not include any details. Such as impersonating is a violation. It does not have any information on how what, to whom, etc. there are 3 most comment points of interest in policies. I will discuss it in details.
First is, security levels which are in multilevel security models. This explains having different authorities to a different set of people. Such as, the employee can view his or her attendance time, and the HR department has the authority to view and modify data when necessary. But they also have certain limitations.
The second point of interest is, separation of duty which is explained in the Clark-Wilson model. If we take a pharmacy as an example, we give the list to give us the medicine to one person. And then we pay the amount to another person and then we collect the medicine from another. Have you wondered why all these separations of duty? This is because to eliminate corruption. The duties are assigned without overlapping so that each person is responsible for their work separately.
The third is a conflict of interest in the Chinese wall model. Which means the same person cannot play different roles if they have different policies for the roles. If you are the manager of a company and your spouse is in a lower position in the same company you cannot pay the manager and husband role in the company. Because you may expose the confidential information to a lower position employee while been the spouse. That is what it is meant by conflict of interest.
What are the types of security policies?
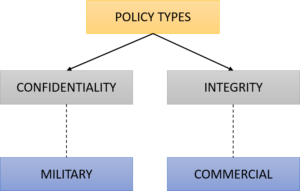
There are two main types of security policies.
- Confidential policy
- Integrity policy
Confidentiality policy protects the confidentiality of the information. Military security policy falls under this category. If the data is leaked to the enemy the military becomes weak. So they concern more about confidentiality.
And the integrity policy protects the integrity factor. The commercial security policy is a subcategory of this. Which means you cannot tell a price to the customer and sell it to another price. Which violated the data modification or integrity.
What is the connection between integrity and transaction in Security Policies?
When we do a bank transaction first is checks for the available balance. Which was a constant from the previous transaction. Then the money is given and the price is reduced. A transaction begins from a consistent state always. And then when the actions related to the transaction is being performed they should make sure it is done in completion. If you withdrew money and the price is not deducted, then there is an issue. So they should make sure it is done in completion. If the transaction succeeds it goes to a new consistent state. And if it fails the system reverts and goes back to the previous consistent state.
Conclusion
In this article, I explained to you how security policies are affected in confidentiality, integrity, and availability. Furthermore, how the policy models affect and the points of interest in these models. And also the types of security policy along with the connection of integrity and transaction.